Though we are recovering from the worst pandemic, cyber threats have shown no sign of downshifting, and cybercriminals are still not short of malicious and advanced ways to achieve their goals.
The Global Threat Landscape Report indicates a drastic rise in sophisticated cyberattacks targeting digital infrastructures, organizations, and individuals in 2021. Threats can take different forms with the intent to commit fraud and damage businesses and people. Ransomware, DDoS attacks, phishing, malware, and man-in-the-middle attacks represent the greatest threat to businesses today.
When new threats emerge, attackers take advantage of them – however, most businesses are only aware of the current threats.
Organizations struggle to address these threats due to their resource sophistication and their lack of understanding of evolving threat landscapes. For these reasons, organizations need visibility on the advanced threats especially targeting their infrastructure. This article will outline the evolution in the cyber threat landscape 2021.
Evolving Threat Landscape – Find Out What You Don't Know
1 — Ransomware
Ransomware is still a common and evolving cyber security threat with several highly publicized incidents. Ransomware incidents affect organizations, businesses, and individuals resulting in financial loss, operational disruptions, and data exfiltration. Compromise through internet-facing vulnerabilities & misconfigurations, third parties & managed service providers, Remote Desktop Protocol (RDP) and phishing emails remain the most common infection vectors.
The occurrence of extortion schemes has increased from single to multiple schemes during 2021. After initially encrypting sensitive information from the victim and threatening to reveal it publicly unless a ransom is paid, attackers are now targeting the victim's partners and customers for ransom to maximize their profits.
New research from Coalition revealed that there was a 170% increase in the average ransom demand in the first half of 2021 compared to last year.
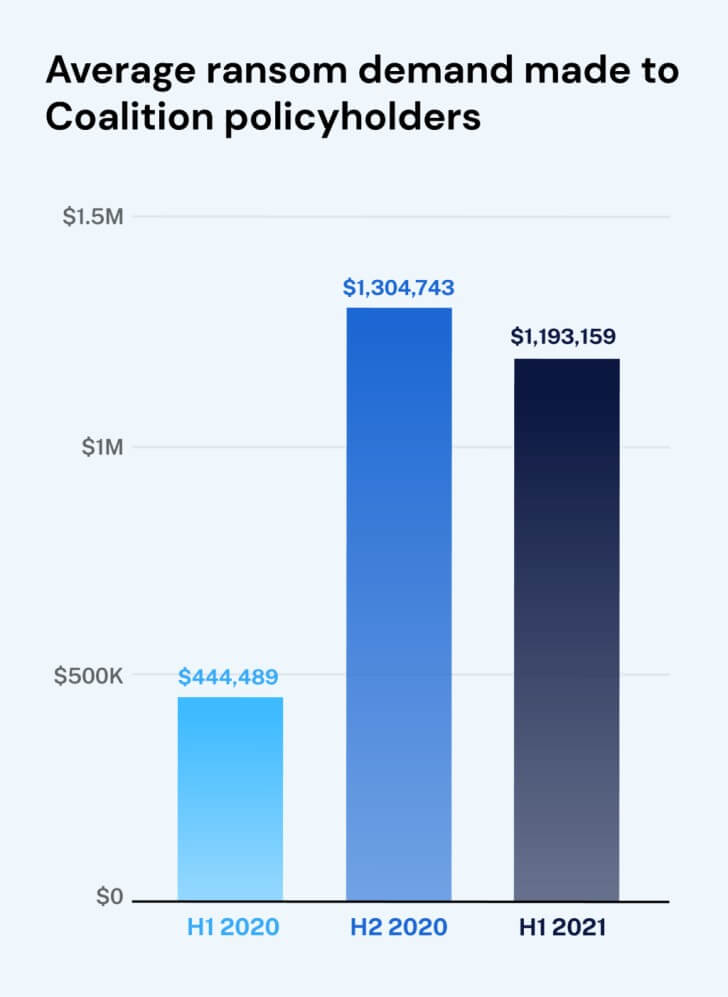 |
| Image source: venturebeat |
It is likely to hit $100 million in 2022 – according to the ENISA Threat Landscape 2021.
Moreover, cryptocurrency becomes the choice of pay-out method because it promises a secure, fast, and anonymous channel for money transactions. Also, attackers shifted from Bitcoin to Monero as their choice due to its enhanced anonymity.
Recommendations to prevent being a victim:
- Security awareness training
- Use secure websites
- Defense-in-depth cybersecurity strategy
- Vulnerability assessment & penetration testing
2 — Cryptojacking
Another attack trend in 2021 is cryptojacking, which is associated with the expanding instability in the cryptocurrency market. Given the anonymity of cryptocurrencies, it has become a convenient and attractive means of exchange by attackers. In this attack, cybercriminals deploy hidden cryptojacking software onto the target's devices, which steals from a cryptocurrency wallet. Siloscape, a new malware, which emerged in June 2021 targets Windows containers and creates malicious containers, loads cryptocurrency miners, which identify and steal cryptocurrency.
Recommendations to counteract cryptojacking:
- Implement web filters and blacklist IP addresses from cryptomining IP pools
- Develop patches against well-known exploits
- Implement a robust vulnerability management program
3 — Data Breaches
Sensitive data being stolen from organizations or users is nothing new, but how threat actors approach it has evolved. Just as organizations embrace new technologies to survive in the digital landscape, threat actors also harness sophisticated methods to exploit attacks – Deepfake technology, for example.
Though it's not a new concept, it has evolved significantly. With MI and AI, Deepfake technology enables the digital creation of an individual's likeness, which can then be used to impersonate the victim. AI and ML tools make it possible to make artificial versions of any voice or any video.
Cybercube's security researchers alerted that deep fake audio and video content could become a major cyber threat to businesses worldwide. Also, the widespread damage associated with this pretended content is expected to increase in the coming years. It is also expected that the enhanced dependence on video-based communication is the major factor that motivates attackers to focus more on Deepfake technology.
Recommendations for Deepfake Monitoring and Removal:
- Improved digital archiving to identify the fake video and fake voice clips
- Implement Content Authenticity Initiative to validate the creator as well as origin of data
4 — Botnets
Newer botnets continue to emerge as old ones keep transforming to sidestep the current security solutions. This is because cyber-criminals see a new paradigm with botnets-as-a-service where bonnets can be leased/sold to corporations or individuals for nefarious uses and financial benefits.
Furthermore, the existence of botnets in the cloud and mobile environment proposes a new possibility that they may soon be able to learn and exploit the weakness on their own in the patterns of user interactions. The increased adoption of IoT and the lack of security when they are developed as well as deployed presents another feasible frontier for botnet proliferation.
A recent report revealed there is a 500% rise in overall IoT attacks by prominent IoT botnets like Mirai and Mozi.
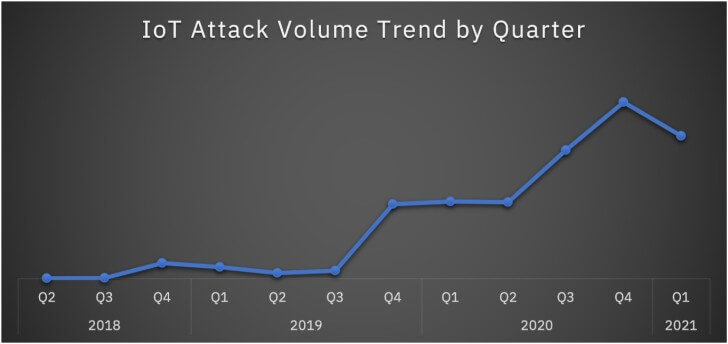 |
| Image source: Security Intelligence |
In 2020, the Mozi botnet attackaccounted for 89% of the IoT attacks – according to X-Force research. In addition to Mozi, several other botnets continue to target the IoT landscape. Ecobot, Zeroshell, Gafgyt, and Loli are four notable botnets impacting businesses all over the world.
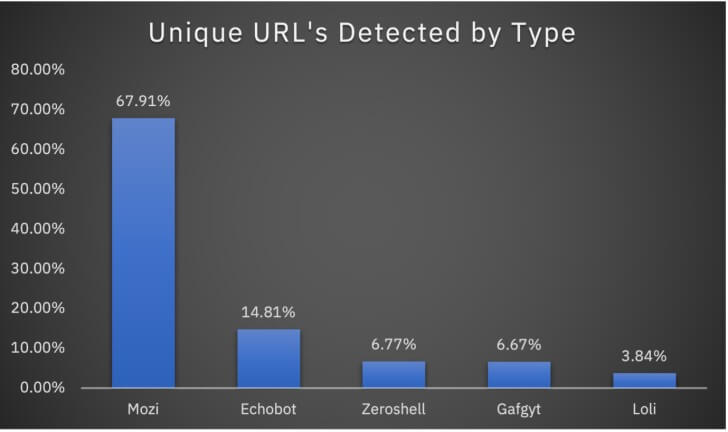 |
| Image source: Security Intelligence |
Recommendations to fight back:
- Employ penetration testing
- Change your default IoT setting when installing any new device
- Implement a powerful patch management program
- Practice effective bot protection and mitigation strategy
The Big Picture
New cyber threats are being detected all the time, and they possess the potential to affect any operating system, including Linux, Windows, iOS, Mac OS, and Android. Additionally, new threats vectors are evolving due to potential vulnerabilities in the continuous adoption of remote working and a growing number of IoT devices being connected.
This cyber threat landscape evolution has forced enterprises to upgrade their vulnerability management program, security tools, processes, and skills to stay ahead. Indusface AppTrana, a fully managed Web Application and API protection (WAAP)addresses these challenges and speeds up threat detection and response.
If you want to be proactive and actionable in protecting your information, stay aware of the recent cyber security threat landscape!
via https://www.AiUpNow.com
November 11, 2021 at 04:36AM by noreply@blogger.com (The Hacker News), Khareem Sudlow
