New dangers, old tricks.
What you need to know
- The Microsoft 365 Defender Threat Intelligence Team has made a post to raise awareness about the increased prevalence of HTML smuggling.
- HTML smuggling has the capacity to bypass many of the filters typically used to protect against dangerous files.
- Advanced though the technique may be, its activation still relies on the oldest trick in the book: Requiring a user to click on something they shouldn't.
Microsoft wants to make sure tech aficionados remain vigilant of the latest cyber threats, including HTML smuggling. HTML smuggling is a threat type the Microsoft 365 Defender Threat Intelligence Team has seen show up with increasing frequency in attacks looking to offload remote access Trojans (RATs) and banking malware onto unsuspecting targets. Threat actors such as the ones behind the massive SolarWinds drama of 2020 and 2021 are an example of those utilizing HTML smuggling.
Microsoft crafted a lengthy blog post on the subject, outlining what the threat is, how it endangers users, and what it looks like in the wild. A chunk of the content is highly technical, but there's a lot of digestible, informative detail in there as well. Here's an excerpt:
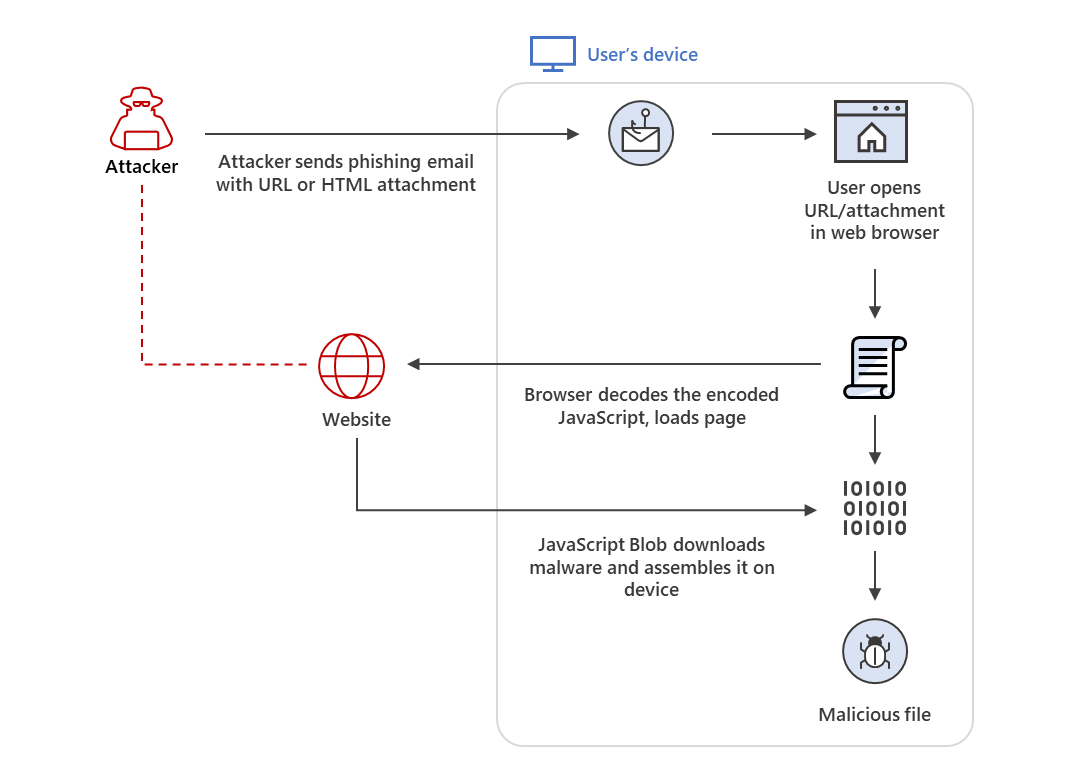
As the name suggests, HTML smuggling lets an attacker "smuggle" an encoded malicious script within a specially crafted HTML attachment or web page. When a target user opens the HTML in their web browser, the browser decodes the malicious script, which, in turn, assembles the payload on the host device. Thus, instead of having a malicious executable pass directly through a network, the attacker builds the malware locally behind a firewall.
Spooky stuff, right? However, though that paragraph makes the threat easy to comprehend, it also highlights why this may not end up being a threat at all for a lot of people: It requires a voluntary click. And a lot of the time, an email packing danger is poorly written enough to unintentionally warn you in advance.
With that said, be sure to check out Microsoft's blog post for the full scoop on how HTML smuggling campaigns attempt to dupe users into exposing their machines. Sometimes, malicious parties can be pretty convincing.
via https://AiUpNow.com November 12, 2021 at 04:24PM by Robert Carnevale, Khareem Sudlow,